|
Frequently
Asked Questions
TupSight
2.6
1.
How TupSight intercepts data of computer communications and enforces
employee Internet policies?
TupSight
boasts
the broadest operation spectrum among the EIM (Employee
Internet Management) products commercially available.
1)
Gateway Mode: This is the default operation mode of
TupSight. The NAT gateway technology embedded in the software
enables a reliable LAN infrastructure/hardware-independent web
monitoring and control at the Internet doorsteps.
2)
Promiscuous Mode: In the early days of computer networking, the sharing nature of communication channels on a local
computer network made packet sniffing possible, by which an intruding hacker picked up passwords and other useful information, and a network administrator diagnosed and
trouble-shooted network traffic (see http://www.faqs.org/faqs/computer-security/sniffers/). Most of the local networks were based on Ethernet, a
"shared medium" in which packet information is broadcast to all the hosts on the same segment, and interfaces, such as
network interface cards (NICs), are designed to bypass the packets not
destined to them. A sniffer program, however, turns a host into promiscuous mode, capturing all the packets for further decoding and data-mining.
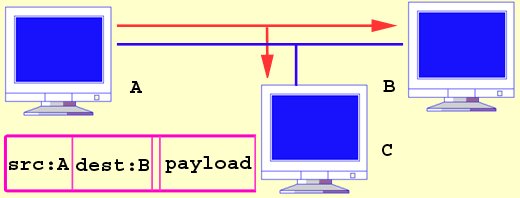
Fig.
1 C sniffs A's packets.
In
today's de facto switched Ethernet environment where switches are used to connect the Ethernet modes together, one
can realize the data capture using an old-fashioned shared
Ethernet hub or via the management port of a switch (It
sometimes is called "port mirroring," "port
monitoring," "Roving Analysis" by 3Com,
or "Switched Port Analyzer" or
"SPAN" by Cisco.). See more detailed below in the
TupInsight FAQ section.
3)
Bridge Mode: This mode is also called “a machine-in–the-middle.” There is a bridging capability called the “Network Bridge” built into Windows
XP and Server 2003. This is a feature of the Network Connections folder that allows a machine with two network interface cards
(NICs) to act as a transparent bridge, connecting different local area network (LAN) segments and capturing all the traffic to and from one
segment. Therefore, the TupSight machine acts in effect as the
"physical" gateway for the network segment
following. For its configuration simplicity and minimum
hardware requirements (2 NICs), the bridge mode is strongly
recommended by us for monitoring and control tasks without
changing much of the existent networking structure (See What's
New File included in the same installation package.)
Fig
2. A machine with two network interface cards (NICs) can be used as a transparent bridge,
capturing all the traffic to and from a single machine or a network segment.
4)
Side-Route Mode: An add-on switch-sniffer program of
TupSight sets up a "virtual" gateway via which all
the Internet communications are captured.
2.
When I install TupSight, a warning window pops up stating that the
software has not passed Windows Logo testing to verify its compatibility.
TupSight
is based on NDIS (Network Driver Interface Specification) as the
application programming interface (API) for network interface cards (NICs),
and a virtual NIC has been created for its operation. Just single-click
the “Continue Anyway” button each time the “Hardware
Installation” warning appears until the end of installation.
3.
Why the data captured by TupSight are from/for my local host but other
computers?
TupSight
has two operation modes, i.e., the gateway mode and the side-route mode.
By default, TupSight operates in the gateway mode, acting as an Internet
gateway for the LAN. When working in the gateway mode, you must configure
the default gateway IP address for other computer hosts so that TupSight
can provide them with Internet connection.
When
working in the side-route mode, just input the router IP address to Gateway
IP on the “Options” window, and click on Acquire MAC
Address.
4.
After the computer hosts to be monitored are selected in the
side-route mode, they are not able to visit the Internet.
You
should check whether the external NIC and IP address are correctly
selected.
1)
Logon the console as the system administrator.
2)
Open Operation View from the left bottom corner on the
console.
3)
Single-click Config.
4)
Check whether the external NIC and IP address are correctly
selected.
Important
Notes:
1)
If there is a proxy program installed (usually on a server machine) and
you want to install TupSight on the same server,
please turn off or uninstall the program to avoid the disruption of the
Internet connection, as a result of potential conflicts, or select any
other PC to install TupSight.
2)
On a LAN with an application-specific proxy server, If you choose to monitor
this
proxy machine in the side-mode, it sometimes will disrupt the Internet
connection. Please proceed with caution.
*
*
*
*
*
*
TupInsight
3.2 (All the functions are now
integrated into TupSight)
1.
What is TupInsight? Is there a difference between it and a spyware-based monitoring program?
TupInsight
is an easy-to-install and –navigate Internet activity monitoring and web
access control system. It uses a computer on a local area network (LAN)
not only to monitor and record other hosts’ web behaviors, but also to
restrict online activities according to customized filtering Internet
policies.
TupInsight
is an eavesdropping program that uses a packet sniffer to capture and
analyze communication traffic over a network. This is very similar to wiretapping
of voice transmission, or listening in on other people’s telephone conversations. On the other
hand, a spyware-based Internet monitoring program, such as the well-known Eblaster or Spector from
spectorsoft or Insight from Trisys, tracks a target’s web use or even general computer use by
installing itself on the computer and sending the information via the network back to the program’s
installer. This is much similar to implanting a bugging device on someone’s phone receiver.
Like
an implanted “bug,” spyware can be detected and removed from a
computer using anti-spyware programs, and the tracked information blocked using a firewall
that monitors outgoing connections from the computer.
Moreover,
another function of TupInsight, with the same importance as Internet
activity monitoring, is to tailor the online access control for the whole LAN on
the level of individual computer hosts.
2.
What are the major functions and features of TupInsight?
The
main functions and features of TupInsight can be summarized as follows:
A.
Capturing all Emails sent/received on the whole local network
TupInsight
records in real-time all the Emails sent/received (including POP3/SMTP and
HTTP protocols), and displays information such as MAC (Media Access Control)
address (or adapter address), IP address, time sent/received, title, sender/receiver,
attachment(s), content, and size.
B.
Snapshoting all the webpages viewed on the whole local network and
copying all the
uploaded/downloaded files (FTP protocol)
TupInsight
provides the snapshots of viewed webpages for an administrator to preview
and stores copies of all the FTP files. It also shows other information
such as title, site, visited time, and size.
C.
Monitoring chat sessions (such as Yahoo, AOL, MSN, and ICQ), game
activities, and other use of online applications self-definable by the
administrator
TupInsight
logs online activities to show the host information, tool used, time
online/offline, and data flow.
D.
Enforcing web access control according to the administrator’s
customization
TupInsight
can freely set privilege rights of web access for and monitoring action on
different classes of hosts in detail. It restricts all or specific online activities
for an individual host, a workgroup, or the whole network, in specific time periods, with preset
blocking lists. TupInsight has the filtering function to forgo monitoring a small special group of
hosts.
E.
Scanning and detecting host names for networked computer
TupInsight
automatically collects and analyzes the available data of computers on the
whole local network to reveal their host names, IP addresses, and MAC
addresses, and classifies the captured messages into categories for
different hosts.
F.
Based on the client/server architecture to support distributed
management of data
TupInsight
adopts the separation of server and client program to achieve levels of
data distribution.
G.
Featuring an easy-to-navigate user interface
TupInsight
implements a hierarchical design in order to group related items together.
Its straightforward interface makes it easy to add, view, edit, and categorize
data and information.
3.
What differentiate TupInsight from the similar products?
From
the very beginning of developing the product, what TupInsight had
envisioned was a feature that would allow a small & midsize business
owner or executive director in an organization to do Internet monitoring
and blocking without third-party participation, while enabling distributed
management of data by sharing different levels of access privileges with
their subordinate managers. Indeed, a complicated product, such as
Websense Enterprise, is gorgeous, but it is also at an unbelievable cost
(as compared to that of TupInsight) and needs to add a dedicated IT staff
operating and maintaining the system.
Furthermore,
the hierarchical design of TupInsight and its straightforward interface
make the task of employee Internet management (EIM) very nearly painless.
4.
Is it legal to monitor employees’ Internet habits at work?
“Federal
law here in the U.S. clearly states that the computer system is the
property of the employer and as such the employer has the right to monitor all e-mail
activity and Internet activity,” according to Nancy Flynn, executive director of The ePolicy Institute, a
Columbus, Ohio-based consulting firm, and author of “E-Mail Rules.”
5.
Why the data captured by TupInsight are from/for my local host but other computers?
If
properly installed, TupInsight (of the unlimited version) should catch
data from all the computer hosts on a LAN. Since TupInsight is an
eavesdropping program, whenever possible the TupInsight engine is always
installed on the gateway machine (using NAT or proxy) so as to capture
data from all the computer hosts on the local network. If the gateway
device is a router rather than a computer, the engine should be installed on a host sharing the same
network segment with the router.
If
only the data from/for one computer (in your case, the local host) are
shown on the TupInsight console, the most probable explanation is that your local host where the
TupInsight engine is installed is connected to the LAN via a switch, a
device that filters and only forwards packets to the designated host.
The
following three schemes explain how to select a computer host for the
TupInsight installation, with Fig. 3 representing the most common
solution.
Case
one: If the networking infrastructure is a traditional shared
hub-based LAN, the TupInsight engine can be installed on any computer host on the network. See Fig. 1.
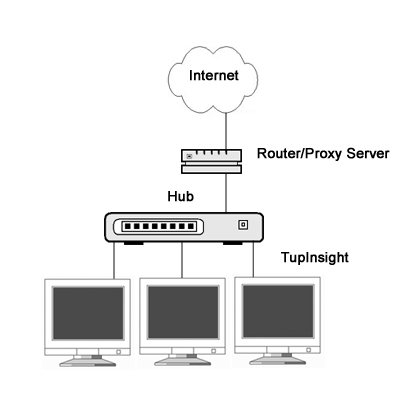
Fig.
1. On a traditional shared hub-based LAN, the engine can be installed on
any host machine.
Case
two: The switched infrastructure is now the de facto technique used to
build local area networks. Unlike hubs, switches
prevent promiscuous sniffing. However, you can still install the TupInsight program on your Internet gateway, a proxy server or a PC shared
the same Ethernet segment with the router (see Case three). Any Internet traffic will pass
through the gateway and therefore TupInsight could catch/restrict them. Since most modern switches
now support “port mirroring,” it also allows a network administrator to monitor LAN
traffic on any computer connected to one designated switch port. To select
a switch follow the link SwitchReference.
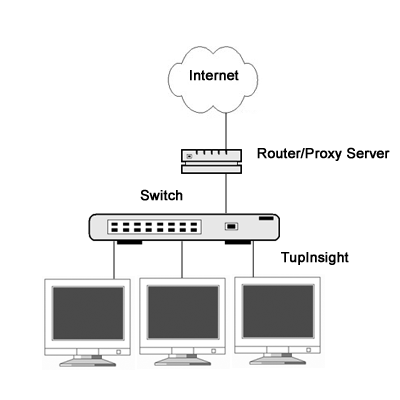
Fig.
2. On a switched LAN, the engine is installed on the gateway machine or a
host connected to the “management port” of the top-level switch.
Case
three: If the Internet gateway is a router rather than a computer, the
simplest and most common solution to capture and block web traffic is to place a shared
hub between the router and the top-level switch, as shown in Fig. 3. For any Internet bandwidth less
than 5 Mbps, as in the case of most small & midsize business networking infrastructures, this
will not exert any negative impact on the Internet access. The typical bandwidth for those networks is
less than 1.5 Mbps. Unfortunately, many "hubs" are actually switches these days. The
following useful links, HubReference,
Capture
Setup, and CaptureSetup/Ethernet,
tell you how to select a real hub, rather than a fake one, and how to setup a capture.
We
have some real Ethernet hubs (NETGEAR DS series) in stock, you can contact
us @support.
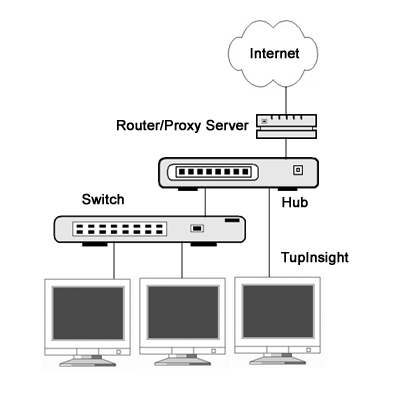
Fig.
3. If the Internet gateway is not a computer, the most common solution is
to add a shared hub between the router and the top-level switch.
6.
Why
the TupInsight program installed on my computer could not capture any data at all?
There
are several possibilities:
1.
You did not restart the PC after the installation of the TupInsight
engine. Certainly, you can always manually start the engine, without shutting down a PC, from
Services in the Administrative Tools dialog from the Windows Control Panel.
2.
You did not set up the monitoring adapter. Here, the monitoring
adapter is the network interface card (NIC) on the host where the
TupInsight is installed. If there are two adapter cards on the host, e.g.,
one for the internal and the other external connection, you should select
the one connected to the local network.
3.
You did not configure the connection ports to be monitored on a LAN
when using a non-NAT proxy server for Internet connection sharing.
4.
Although the packet-sniffing program on which the TupInsight is
based supports most of network adapters, it does not work for some specific wireless,
USB, or
PCMCIA cards.
5.
Improper firewall settings interfere the operation of TupInsight programs.
7.
How can I upgrade TupInsight to a newer version?
You
can follow the following procedure:
1.
Download the newer version of TupInsight from www.tupsoft.com.
2.
Backup the monitoring settings into a file.
3.
Uninstall the existing TupInsight programs.
4.
Install the newer programs.
5.
Restore the monitoring settings from the downloaded file in Step 2.
|
Search Keywords:
|
NAT Gateway
|
NAT Gateway
|
NAT Gateway
|
NAT Gateway
|
NAT Gateway
|
NAT Gateway
|
NAT Gateway
|
NAT Gateway
|
NAT Gateway
|
|
Search Keywords:
|
Proxy Server
|
Proxy Server
|
Proxy Server
|
Proxy Server
|
Proxy Server
|
Proxy Server
|
Proxy Server
|
Proxy Server
|
Proxy Server
|
|
Search Keywords:
|
NAT Router
|
NAT Router
|
NAT Router
|
NAT Router
|
NAT Router
|
NAT Router
|
NAT Router
|
NAT Router
|
NAT Router
|
|
Search Keywords:
|
DNS Forwarding
|
DNS Forwarding
|
DNS Forwarding
|
DNS Forwarding
|
DNS Forwarding
|
DNS Forwarding
|
DNS Forwarding
|
DNS Forwarding
|
DNS Forwarding
|
|
Search Keywords:
|
Port Mapping
|
Port Mapping
|
Port Mapping
|
Port Mapping
|
Port Mapping
|
Port Mapping
|
Port Mapping
|
Port Mapping
|
Port Mapping
|
|
Search Keywords:
|
Reverse Proxy
|
Reverse Proxy
|
Reverse Proxy
|
Reverse Proxy
|
Reverse Proxy
|
Reverse Proxy
|
Reverse Proxy
|
Reverse Proxy
|
Reverse Proxy
|
|
Search Keywords:
|
Internet Connection Sharing
|
Internet Connection Sharing
|
Internet Connection Sharing
|
Internet Connection Sharing
|
Internet Connection Sharing
|
Internet Connection Sharing
|
Internet Connection Sharing
|
Internet Connection Sharing
|
Internet Connection Sharing
|
|
Search Keywords:
|
Internet Activity Monitoring
|
Internet Activity Monitoring
|
Internet Activity Monitoring
|
Internet Activity Monitoring
|
Internet Activity Monitoring
|
Internet Activity Monitoring
|
Internet Activity Monitoring
|
Internet Activity Monitoring
|
Internet Activity Monitoring
|
|
Search Keywords:
|
Parental Internet Monitoring
|
Parental Internet Monitoring
|
Parental Internet Monitoring
|
Parental Internet Monitoring
|
Parental Internet Monitoring
|
Parental Internet Monitoring
|
Parental Internet Monitoring
|
Parental Internet Monitoring
|
Parental Internet Monitoring
|
|
Search Keywords:
|
Internet Filtering
|
Internet Filtering
|
Internet Filtering
|
Internet Filtering
|
Internet Filtering
|
Internet Filtering
|
Internet Filtering
|
Internet Filtering
|
Internet Filtering
|
|
Search Keywords:
|
Internet Activity Statistics
|
Internet Activity Statistics
|
Internet Activity Statistics
|
Internet Activity Statistics
|
Internet Activity Statistics
|
Internet Activity Statistics
|
Internet Activity Statistics
|
Internet Activity Statistics
|
Internet Activity Statistics
|
|
Search Keywords:
|
Employee Internet Management
|
Employee Internet Management
|
Employee Internet Management
|
Employee Internet Management
|
Employee Internet Management
|
Employee Internet Management
|
Employee Internet Management
|
Employee Internet Management
|
Employee Internet Management
|
|
Search Keywords:
|
Web Access Control
|
Web Access Control
|
Web Access Control
|
Web Access Control
|
Web Access Control
|
Web Access Control
|
Web Access Control
|
Web Access Control
|
Web Access Control
|
|
Search Keywords:
|
Online Restriction
|
Online Restriction
|
Online Restriction
|
Online Restriction
|
Online Restriction
|
Online Restriction
|
Online Restriction
|
Online Restriction
|
Online Restriction
|
|
Search Keywords:
|
Network Monitoring
|
Network Monitoring
|
Network Monitoring
|
Network Monitoring
|
Network Monitoring
|
Network Monitoring
|
Network Monitoring
|
Network Monitoring
|
Network Monitoring
|
|
Search Keywords:
|
URL Block
|
URL Block
|
URL Block
|
URL Block
|
URL Block
|
URL Block
|
URL Block
|
URL Block
|
URL Block
|
|
Search Keywords:
|
Email Capture
|
Email Capture
|
Email Capture
|
Email Capture
|
Email Capture
|
Email Capture
|
Email Capture
|
Email Capture
|
Email Capture
|
|
Search Keywords:
|
Chat Log
|
Chat Log
|
Chat Log
|
Chat Log
|
Chat Log
|
Chat Log
|
Chat Log
|
Chat Log
|
Chat Log
|
|
Search Keywords:
|
MSN Recorder
|
MSN Recorder
|
MSN Recorder
|
MSN Recorder
|
MSN Recorder
|
MSN Recorder
|
MSN Recorder
|
MSN Recorder
|
MSN Recorder
|
|
Search Keywords:
|
Yahoo Messenger Sinffer
|
Yahoo Messenger Sinffer
|
Yahoo Messenger Sinffer
|
Yahoo Messenger Sinffer
|
Yahoo Messenger Sinffer
|
Yahoo Messenger Sinffer
|
Yahoo Messenger Sinffer
|
Yahoo Messenger Sinffer
|
Yahoo Messenger Sinffer
|
|
Search Keywords:
|
Skype Logger
|
Skype Logger
|
Skype Logger
|
Skype Logger
|
Skype Logger
|
Skype Logger
|
Skype Logger
|
Skype Logger
|
Skype Logger
|
|
Search Keywords:
|
Computer Activity Log
|
Computer Activity Log
|
Computer Activity Log
|
Computer Activity Log
|
Computer Activity Log
|
Computer Activity Log
|
Computer Activity Log
|
Computer Activity Log
|
Computer Activity Log
|
|
Search Keywords:
|
Real Time Monitoring
|
Real Time Monitoring
|
Real Time Monitoring
|
Real Time Monitoring
|
Real Time Monitoring
|
Real Time Monitoring
|
Real Time Monitoring
|
Real Time Monitoring
|
Real Time Monitoring
|
|
Search Keywords:
|
Screen Tracking
|
Screen Tracking
|
Screen Tracking
|
Screen Tracking
|
Screen Tracking
|
Screen Tracking
|
Screen Tracking
|
Screen Tracking
|
Screen Tracking
|
|
Search Keywords:
|
Software Compliance
|
Software Compliance
|
Software Compliance
|
Software Compliance
|
Software Compliance
|
Software Compliance
|
Software Compliance
|
Software Compliance
|
Software Compliance
|
|
Search Keywords:
|
Data Protection Security
|
Data Protection Security
|
Data Protection Security
|
Data Protection Security
|
Data Protection Security
|
Data Protection Security
|
Data Protection Security
|
Data Protection Security
|
Data Protection Security
|
|
Search Keywords:
|
Acceptable Computing
|
Acceptable Computing
|
Acceptable Computing
|
Acceptable Computing
|
Acceptable Computing
|
Acceptable Computing
|
Acceptable Computing
|
Acceptable Computing
|
Acceptable Computing
|
|
Search Keywords:
|
Employee Investigative Operation
|
Employee Investigative Operation
|
Employee Investigative Operation
|
Employee Investigative Operation
|
Employee Investigative Operation
|
Employee Investigative Operation
|
Employee Investigative Operation
|
Employee Investigative Operation
|
Employee Investigative Operation
|
|
Search Keywords:
|
Switch Sniffer
|
Switch Sniffer
|
Switch Sniffer
|
Switch Sniffer
|
Switch Sniffer
|
Switch Sniffer
|
Switch Sniffer
|
Switch Sniffer
|
Switch Sniffer
|
|
Search Keywords:
|
Packet Sniffing
|
Packet Sniffing
|
Packet Sniffing
|
Packet Sniffing
|
Packet Sniffing
|
Packet Sniffing
|
Packet Sniffing
|
Packet Sniffing
|
Packet Sniffing
|
|
Search Keywords:
|
Ethernet Capture
|
Ethernet Capture
|
Ethernet Capture
|
Ethernet Capture
|
Ethernet Capture
|
Ethernet Capture
|
Ethernet Capture
|
Ethernet Capture
|
Ethernet Capture
|
|
Search Keywords:
|
Network Tap
|
Network Tap
|
Network Tap
|
Network Tap
|
Network Tap
|
Network Tap
|
Network Tap
|
Network Tap
|
Network Tap
|
|
Search Keywords:
|
MITM
|
MITM
|
MITM
|
MITM
|
MITM
|
MITM
|
MITM
|
MITM
|
MITM
|
|
Search Keywords:
|
ARP Poisoning
|
ARP Poisoning
|
ARP Poisoning
|
ARP Poisoning
|
ARP Poisoning
|
ARP Poisoning
|
ARP Poisoning
|
ARP Poisoning
|
ARP Poisoning
|
|
Search Keywords:
|
ARP Spooling
|
ARP Spooling
|
ARP Spoofing
|
ARP Spoofing
|
ARP Spoofing
|
ARP Spoofing
|
ARP Spoofing
|
ARP Spoofing
|
ARP Spoofing
|
|
Search Keywords:
|
ARP Firewall
|
ARP Firewall
|
ARP Firewall
|
ARP Firewall
|
ARP Firewall
|
ARP Firewall
|
ARP Firewall
|
ARP Firewall
|
ARP Firewall
|
|
Search Keywords:
|
MAC Flooding
|
MAC Flooding
|
MAC Flooding
|
MAC Flooding
|
MAC Flooding
|
MAC Flooding
|
MAC Flooding
|
MAC Flooding
|
MAC Flooding
|
|
Search Keywords:
|
Promiscuous Mode
|
Promiscuous Mode
|
Promiscuous Mode
|
Promiscuous Mode
|
Promiscuous Mode
|
Promiscuous Mode
|
Promiscuous Mode
|
Promiscuous Mode
|
Promiscuous Mode
|
|
Search Keywords:
|
Block Instant Messaging
|
Block Instant Messaging
|
Block Instant Messaging
|
Block Instant Messaging
|
Block Instant Messaging
|
Block Instant Messaging
|
Block Instant Messaging
|
Block Instant Messaging
|
Block Instant Messaging
|
|
Search Keywords:
|
Web Content Monitoring
|
Web Content Monitoring
|
Web Content Monitoring
|
Web Content Monitoring
|
Web Content Monitoring
|
Web Content Monitoring
|
Web Content Monitoring
|
Web Content Monitoring
|
Web Content Monitoring
|
|
Search Keywords:
|
Employee Computer Abuse
|
Employee Computer Abuse
|
Employee Computer Abuse
|
Employee Computer Abuse
|
Employee Computer Abuse
|
Employee Computer Abuse
|
Employee Computer Abuse
|
Employee Computer Abuse
|
Employee Computer Abuse
|
|
Search Keywords:
|
Internet Policy Enforcement
|
Internet Policy Enforcement
|
Internet Policy Enforcement
|
Internet Policy Enforcement
|
Internet Policy Enforcement
|
Internet Policy Enforcement
|
Internet Policy Enforcement
|
Internet Policy Enforcement
|
Internet Policy Enforcement
|
|
Search Keywords:
|
Website Filter
|
Website Filter
|
Website Filter
|
Website Filter
|
Website Filter
|
Website Filter
|
Website Filter
|
Website Filter
|
Website Filter
|
|
Search Keywords:
|
Email Backup
|
Email Backup
|
Email Backup
|
Email Backup
|
Email Backup
|
Email Backup
|
Email Backup
|
Email Backup
|
Email Backup
|
|
Search Keywords:
|
Electronic Evidence
|
Electronic Evidence
|
Electronic Evidence
|
Electronic Evidence
|
Electronic Evidence
|
Electronic Evidence
|
Electronic Evidence
|
Electronic Evidence
|
Electronic Evidence
|
|
Search Keywords:
|
E-Discovery
|
E-Discovery
|
E-Discovery
|
E-Discovery
|
E-Discovery
|
E-Discovery
|
E-Discovery
|
E-Discovery
|
E-Discovery
|
|
Search Keywords:
|
Digital Archive
|
Digital Archive
|
Digital Archive
|
Digital Archive
|
Digital Archive
|
Digital Archive
|
Digital Archive
|
Digital Archive
|
Digital Archive
|
|
Search Keywords:
|
IM Recovery
|
IM Recovery
|
IM Recovery
|
IM Recovery
|
IM Recovery
|
IM Recovery
|
IM Recovery
|
IM Recovery
|
IM Recovery
|
|
Search Keywords:
|
Virtual Shredding
|
Virtual Shredding
|
Virtual Shredding
|
Virtual Shredding
|
Virtual Shredding
|
Virtual Shredding
|
Virtual Shredding
|
Virtual Shredding
|
Virtual Shredding
|
|
Search Keywords:
|
Workplace Internet Misuse
|
Workplace Internet Misuse
|
Workplace Internet Misuse
|
Workplace Internet Misuse
|
Workplace Internet Misuse
|
Workplace Internet Misuse
|
Workplace Internet Misuse
|
Workplace Internet Misuse
|
Workplace Internet Misuse
|
|
Search Keywords:
|
Internet Usage Policy
|
Internet Usage Policy
|
Internet Usage Policy
|
Internet Usage Policy
|
Internet Usage Policy
|
Internet Usage Policy
|
Internet Usage Policy
|
Internet Usage Policy
|
Internet Usage Policy
|
|
Search Keywords:
|
Application Program Locker
|
Application Program Locker
|
Application Program Locker
|
Application Program Locker
|
Application Program Locker
|
Application Program Locker
|
Application Program Locker
|
Application Program Locker
|
Application Program Locker
|
|
Search Keywords:
|
PC Activity Checker
|
PC Activity Checker
|
PC Activity Checker
|
PC Activity Checker
|
PC Activity Checker
|
PC Activity Checker
|
PC Activity Checker
|
PC Activity Checker
|
PC Activity Checker
|
|
Search Keywords:
|
Workplace Porn Filter
|
Workplace Porn Filter
|
Workplace Porn Filter
|
Workplace Porn Filter
|
Workplace Porn Filter
|
Workplace Porn Filter
|
Workplace Porn Filter
|
Workplace Porn Filter
|
Workplace Porn Filter
|
|
Search Keywords:
|
Streaming Media Ban
|
Streaming Media Ban
|
Streaming Media Ban
|
Streaming Media Ban
|
Streaming Media Ban
|
Streaming Media Ban
|
Streaming Media Ban
|
Streaming Media Ban
|
Streaming Media Ban
|
|
Search Keywords:
|
Stock Streamer Blocker
|
Stock Streamer Blocker
|
Stock Streamer Blocker
|
Stock Streamer Blocker
|
Stock Streamer Blocker
|
Stock Streamer Blocker
|
Stock Streamer Blocker
|
Stock Streamer Blocker
|
Stock Streamer Blocker
|
|
Search Keywords:
|
Download Restriction
|
Download Restriction
|
Download Restriction
|
Download Restriction
|
Download Restriction
|
Download Restriction
|
Download Restriction
|
Download Restriction
|
Download Restriction
|
|
Search Keywords:
|
PC Screen Tracker
|
PC Screen Tracker
|
PC Screen Tracker
|
PC Screen Tracker
|
PC Screen Tracker
|
PC Screen Tracker
|
PC Screen Tracker
|
PC Screen Tracker
|
PC Screen Tracker
|
|
Search Keywords:
|
USB Lockup
|
USB Lockup
|
USB Lockup
|
USB Lockup
|
USB Lockup
|
USB Lockup
|
USB Lockup
|
USB Lockup
|
USB Lockup
|
|
Search Keywords:
|
Workplace Online Privacy
|
Workplace Online Privacy
|
Workplace Online Privacy
|
Workplace Online Privacy
|
Workplace Online Privacy
|
Workplace Online Privacy
|
Workplace Online Privacy
|
Workplace Online Privacy
|
Workplace Online Privacy
|
|
Search Keywords:
|
School Internet Monitoring
|
School Internet Monitoring
|
School Internet Monitoring
|
School Internet Monitoring
|
School Internet Monitoring
|
School Internet Monitoring
|
School Internet Monitoring
|
School Internet Monitoring
|
School Internet Monitoring
|
|
Search Keywords:
|
Library Online Solution
|
Library Online Solution
|
Library Online Solution
|
Library Online Solution
|
Library Online Solution
|
Library Online Solution
|
Library Online Solution
|
Library Online Solution
|
Library Online Solution
|
|
Search Keywords:
|
Network Surveillance
|
Network Surveillance
|
Network Surveillance
|
Network Surveillance
|
Network Surveillance
|
Network Surveillance
|
Network Surveillance
|
Network Surveillance
|
Network Surveillance
|
|
Search Keywords:
|
Kid PC Activity
|
Kid PC Activity
|
Kid PC Activity
|
Kid PC Activity
|
Kid PC Activity
|
Kid PC Activity
|
Kid PC Activity
|
Kid PC Activity
|
Kid PC Activity
|
|
Search Keywords:
|
EIM Software
|
EIM Software
|
EIM Software
|
EIM Software
|
EIM Software
|
EIM Software
|
EIM Software
|
EIM Software
|
EIM Software
|
|
Search Keywords:
|
Gigabit Ethernet Analyzer
|
Gigabit Ethernet Analyzer
|
Gigabit Ethernet Analyzer
|
Gigabit Ethernet Analyzer
|
Gigabit Ethernet Analyzer
|
Gigabit Ethernet Analyzer
|
Gigabit Ethernet Analyzer
|
Gigabit Ethernet Analyzer
|
Gigabit Ethernet Analyzer
|
|
Search Keywords:
|
Network Performance Tester
|
Network Performance Tester
|
Network Performance Tester
|
Network Performance Tester
|
Network Performance Tester
|
Network Performance Tester
|
Network Performance Tester
|
Network Performance Tester
|
Network Performance Tester
|
|
Search Keywords:
|
Network Testing Products
|
Network Testing Products
|
Network Testing Products
|
Network Testing Products
|
Network Testing Products
|
Network Testing Products
|
Network Testing Products
|
Network Testing Products
|
Network Testing Products
|
|
Search Keywords:
|
Network Protocol Analyzer
|
Network Protocol Analyzer
|
Network Protocol Analyzer
|
Network Protocol Analyzer
|
Network Protocol Analyzer
|
Network Protocol Analyzer
|
Network Protocol Analyzer
|
Network Protocol Analyzer
|
Network Protocol Analyzer
|
|
|
|
|
|
|
|
|
|
|
|
|